For a budding researcher, other people’s PhD papers or dissertations can be a true inspiration and guide along the way. Unfortunately, such dissertations are often hard to find, simply because they more often than not do not appear in bibliographic searches, since they don’t always qualify as valid publications. Fortunately then that some universities keep track of the writings and presentations of their students, researchers or academic staff such that it appears in Google searches. That is how I found Antagonistic gateways in the transport network in a supply chain perspective by Daniel Ekwall, a student at the School of Engineering at University College of Borås, Borås, Sweden.
For a budding researcher, other people’s PhD papers or dissertations can be a true inspiration and guide along the way. Unfortunately, such dissertations are often hard to find, simply because they more often than not do not appear in bibliographic searches, since they don’t always qualify as valid publications. Fortunately then that some universities keep track of the writings and presentations of their students, researchers or academic staff such that it appears in Google searches. That is how I found Antagonistic gateways in the transport network in a supply chain perspective by Daniel Ekwall, a student at the School of Engineering at University College of Borås, Borås, Sweden.
Daniel Ekwall’s thesis combines theories from criminology with theories from logistics and supply chain management to examine cross-over points or antagonistic gateways between the legal and illegal logistics system from a supply chain perspective. In my humble opinion, Antagonistic gateways in the transport network in a supply chain perspective is brilliant and adds considerable new knowlegde to the field of supply chain security.
The thesis consist of a a) thesis section, describing the theoretical framework, the research questions, methodology and approach, the findings and limitations, and b) three papers, submitted to and assumedly accepted by three different an renown journals:
- Differences in Black and White Logistics System Design
- The role of temporary storage from a supply chain perspective
- Cargo theft from supply chains: Crime displacement in logistics
 |
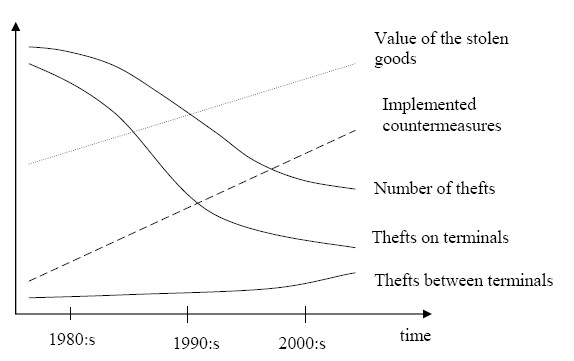 |
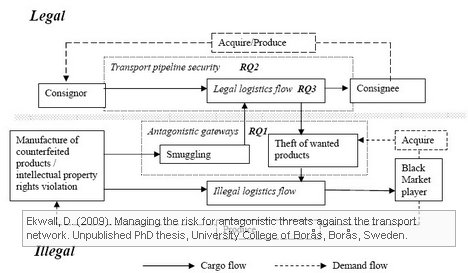
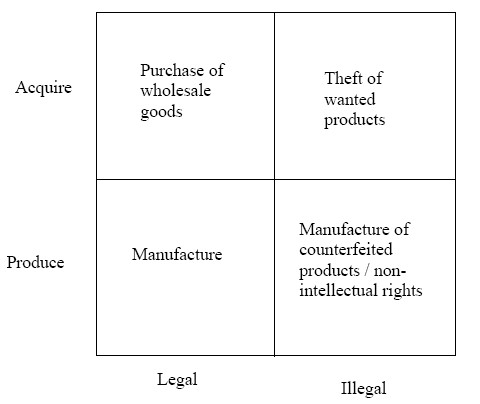
In his conclusion, Ekwall contends that there are basically two types of threats to logistics, theft/sabotage and smuggling. The theft/sabotage problem is directly aimed towards the logistics activities, while smuggling abuses the logistics system for illegal purposes.
To achieve a high overall supply chain performance all processes and activities need to be scheduled and managed, in order to obtain both cost efficiency and short lead-times. In the transport network this is realized by the extended use of time-windows. These windows are scheduled after the needs or demands from the terminal, warehouse or factory’s internal activity, or in other words, the demands from the receiver and not the forwarder or the consignor. This makes the network predictable for all actors involved, including the potential perpetrator. This predictability plays an important role in all potential crimes within the network.
The rigid scheduling in the transport network provides an excellent breeding ground for repeating crime opportunities.
As the perpetrators are becoming more professional, they will also be able to utilize the weak spots in the transport network within their mobility and ability.
The perpetrator’s decision process is the key issue to understand the usage of antagonistic gateways in the transport network. This means that a contextual risk management approach is better to use when preventing the usage of antagonistic gateways.
In essence and over-simplified, if you want to secure your supply chain you have to start thinking like a criminal and analyze where he would be most likely to attack your supply chain (or simply walk in through those antagonistic gateways). However, customer satisfaction and customer demand is what drives the design of the supply chain, which is exactly what creates opportunities for supply chain crimes. Over-securing your supply chain may not be the answer, but securing your weak spots and changing your network setup away from a rigid and predictable schedule will make it harder for potential perpetrators to access those antagonistic gateways.
References
- Ekwall, D. (2009). Managing the risk for antagonistic threats against the transport network. Unpublished PhD thesis, University College of Borås, Borås, Sweden.
- Ekwall, D. (2009). The displacement effect in cargo theft International Journal of Physical Distribution & Logistics Management, 39 (1), 47-62 DOI: 10.1108/09600030910929183
Downloads
Author link
- linkedin.com: Daniel Ekwall