A Wiley book rarely lets you down, and this one doesn’t either. With a refreshing Australian touch, distinctively unlike many American books on the same subject, this 445-page heavy-weight of a book has it all. Security Risk Management – Body of Knowledge, written by Julian Talbot and Miles Jakeman, is a vast and practically all-encompassing repository of knowledge, filled with accepted best practices, innovations and research in the evolving field of security risk management. This book does not have a narrow scope, it is wide open, and it extends towards business continuity, resilience and even supply chain management.
A Wiley book rarely lets you down, and this one doesn’t either. With a refreshing Australian touch, distinctively unlike many American books on the same subject, this 445-page heavy-weight of a book has it all. Security Risk Management – Body of Knowledge, written by Julian Talbot and Miles Jakeman, is a vast and practically all-encompassing repository of knowledge, filled with accepted best practices, innovations and research in the evolving field of security risk management. This book does not have a narrow scope, it is wide open, and it extends towards business continuity, resilience and even supply chain management.
Excellent
This book is brilliant. Developed as an initiative of the Risk Management Institution of Australasia (RMIA), it thoroughly details the security risk management process in an easy-to-read format that can be understood by executive managers and deployed by security risk management practitioners. Indeed, no prior knowledge is required. Accompanied by rich and colorful illustrations on every other page (examples can be seen in the preview below), the message is clear: While today’s business world may be complex, security risk management doesn’t have to follow suit with the same complexity. Yes, risks may be complex, but managing them is not, and this book makes it look easy. Essentially this book provides a mixture of security management, resilience management and business continuity management, and it does so very well. It is a vast book and I can only review so much, but let’s see what the book has to offer.
Security
Security Risk Management, so the book says, is an essential part of any individual’s organization’s or community’s wider risk management activities. Security means
the measures used to protect sensitive organizational assets that collectively create, enable and sustain organizational capability
The fundamental assets that need to be protected, according according to the authors, are: People, Information and Facilities.
Risk matrix
The book uses the traditional risk matrix approach to evaluate probabilities and consequences. What I like here is the division of the impacts that are separated into 6 classes:
- People
- Information
- Property and Equipment
- Reputation
- Finances
- (Business) Operations
For each consequence category, the potential consequences are shown, ranging from insignificant to extensive.
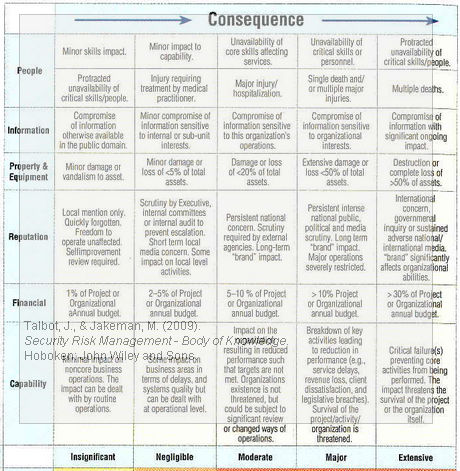
Personally I think environmental impact should have been included here, although implicitly, it may be covered under Reputation. Nonetheless, I think that the incremental worsening of the consequences from left to right is just right for general purposes, but the individual organization will have to set its own increments of course.
Risk metrics
Among other things, the book also features a list of no less than twelve risk definitions, their benefits and potential drawbacks, as seen in the excerpts below:

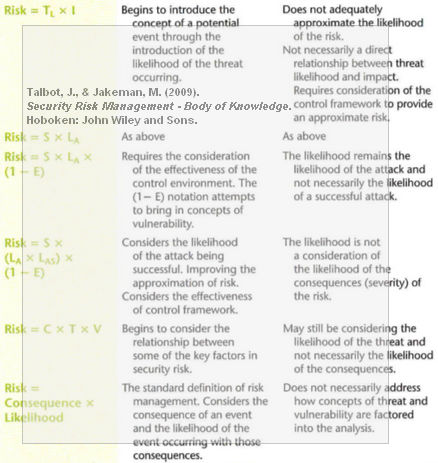
In my mind, this significantly enhances the value of the book, as it allows the decision-maker to evaluate several approaches to risk, and chose the definition that is most useful for one’s own circumstances.
SRM Lexicon
One of the best features of the book is the SRM Lexicon, a 50-page compilation of more than 250 terms and definitions related to security risk management. In fact, the SRM Lexicon can be read entirely on its own, without any reference to the book; it would still make perfect sense. It’s that good.
Security risks in the supply chain
The book contains a rather small, but nevertheless important section on supply chain security risk management. Supply chain security is here seen as a measure for preventing supply chain disruptions, where security (i.e. disruption) risks exist within theses realms:
- Parts or raw material suppliers
- disruption of supply
- Outsourced manufacturers
- production errors, recalls
- Internet service providers
- website downtime or inaccessible e-mail?
- Utility suppliers
- electricity blackout, water contamination?
- Ports, railway stations, airport terminals
- illegal access to products, delays, strikes?
- On-site subcontractors and temp workers
- access to sensitive information or areas (espionage)?
- Document couriers
- loss or unintended distribution of confidential information
- Distributors of products
- tampering with products
These are just some of the examples provided in the book. While the section on supply chain security is brief, it does contain the essentials. Here, as elsewhere in the book, Sheffi’s view of the resilient enterprise permeates much of the authors’ reasonings. The New Zealand research project Resilient Organisations, which has been portrayed time and again on this blog, is also mentioned.
Critique
This is a solid handbook that leaves no ground uncovered. Because it is so comprehensive, after reading the book, I do feel a bit lost…as in “Where do I go from here and where do I start?”. That is where the sample templates are most helpful, as they provide a step-by-step guide, examples and check list towards achieving full security risk management. Besides this, the SRM lexicon and the illustrations make this book more than worthwhile.
Reference
Talbot, J., & Jakeman, M. (2009). Security Risk Management – Body of Knowledge. Hoboken: John Wiley and Sons.
Author links
- juliantalbot.com: Julian Talbot
- linkedin.com: Miles Jakeman
Preview
- books.google.com: SRMBOK
Buy this book
- amazon.com: Security Risk Management Body of Knowledge
Related posts
- husdal.com: ISO 28002 – Supply Chain Security
- husdal.com: Supply Chain Security Management