 Today’s journal article review is an article by professor Göran Svensson from Halmstad University in Sweden. He is one of the first academic contributors to the field of supply chain risk, beginning around 1999. Vulnerability in business relationships was published in 2004, and it came to my attention because a lot of the literature on managaging an mitigating supply chain risk focuses on building relationships with suppliers. Trust and dependence are major components of a dyadic business relationship and therefore, important to discuss.
Today’s journal article review is an article by professor Göran Svensson from Halmstad University in Sweden. He is one of the first academic contributors to the field of supply chain risk, beginning around 1999. Vulnerability in business relationships was published in 2004, and it came to my attention because a lot of the literature on managaging an mitigating supply chain risk focuses on building relationships with suppliers. Trust and dependence are major components of a dyadic business relationship and therefore, important to discuss.
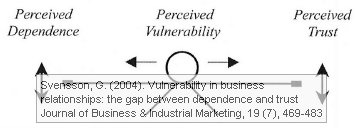
The vulnerability gap
What Svensson postulates is that the the perceived trust and the perceived dependence in business relationships influence the perceived vulnerability. The higher the perceived dependence, the higher the perceived vulnerability. The higher the perceived trust, the lower the perceived vulnerability. Trust and dependence interact with vulnerability such that imbalances on either side can be countered by adding to the other side, like a see-saw. In a relationship with low trust, the degree of dependence should be lowered, in a relationship with high dependence, the degree of trust should be increased.
Trust and dependence
According to Svensson, and based on Swan, a trust relationship is
- Dependable
- Honest
- Competent
- Professional
- Friendly
Based on Hammerkvist, Svensson finds that a dependency relationship has these 5 components
- Technical dependence
- Time (workflow) dependence
- Knowledge dependence
- Social (relationships) dependence
- Economic or judicial dependence
In addition, Svensson brings in two more dependencies in his research:
- Market dependence
- IT dependence
Trust-dependence matrices
Based on a survey among some 100 companies in Sweden Svensson constructs trust-dependence matrices, linking each dependence item with each trust item, for ingoing and outgoing flows.
There are differences between the correlations of individual trust-dependence items, but the overall picture shows a clear linkage between trust and dependence.
Conclusion
Based on his research, Svensson concludes that a favorable vulnerability scenario is indicated by a high level of trust and dependence in both directions. A convenient vulnerability scenario is indicated by a high level of trust towards suppliers and a low level of dependence towards customers. A high level of dependence towards suppliers and a low level of trust towards suppliers would constitute a troublesome vulnerability scenario. A low level of trust and dependence in either direction is seen as a neglectable vulnerability scenario.
Reference
Svensson, G. (2004). Vulnerability in business relationships: the gap between dependence and trust Journal of Business & Industrial Marketing, 19 (7), 469-483 DOI: 10.1108/08858620410564418
Links
- Halmstad University: Göran Svensson‘s homepage
- nordinavia.se: Göran Svensson’s full professional profile and CV
Related
- husdal.com: Trust, control and risk in strategic alliances
- husdal.com: Biting the hand that feeds. Or why all firms are snakes
- husdal.com: Book review: Cooperative strategy