After publishing  A conceptual framework for the analysis of vulnerability in supply chains, Gøran Svensson came up with a 2nd article along the same topic in 2002, entitled A conceptual framework of vulnerability in firms’ inbound and outbound logistics flows. The difference between the two papers is that while the former deals with the inbound flow only, the latter incorporates both the inbound and outbound flow.
A conceptual framework for the analysis of vulnerability in supply chains, Gøran Svensson came up with a 2nd article along the same topic in 2002, entitled A conceptual framework of vulnerability in firms’ inbound and outbound logistics flows. The difference between the two papers is that while the former deals with the inbound flow only, the latter incorporates both the inbound and outbound flow.
Four vulnerability scenarios
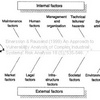
From a vulnerability perspective, both the inbound and outbound flow can be segregated as in [1], where the 2 categories of disturbance (quantitative and qualitative) and the 2 sources of disturbance (atomistic and holistic) create 4 vulnerability scenarios. In order to further refine this conceptual framework. In [2] (this paper), Svensson creates another set of four vulnerability or disturbance scenarios, related to the degree (high or low) of inbound and outbound vulnerability.
Four dimensions
In addition to the 4 scenarios, presented in the framework figure below, Svensson also introduces four principal dimensions that allow for an estimation of the degree of negativity caused by the disturbances:
- Service Level
— the degree of reliability in the supply chain - Deviation
— the degree of non-reliability in the supply chain - Consequence
— the degree of negative impact that disturbances have - Trend
— the degree of consistent direction that disturbances have
These dimension can be used in order to assess the vulnerability in inbound and outbound flows. Applying these dimensions in his research, Svensson then develops the framework for his 4 vulnerability scenarios.
The framework
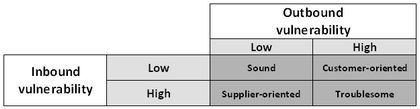
Svenssson (2002) Inbound and outbound vulnerability matrix
Conclusion
The four vulnerability scenarios in the framework clearly designate the direction of the vulnerability as coming from the supplier or going towards the customer. Addressing supplier-oriented vulnerability will be different from addressing customer-oriented vulnerability. In addition the four dimension will assist in analyzing and estimating the degree of vulnerability within each scenario.
References
BACK TO POST [1] Svensson, G. (2000). A conceptual framework for the analysis of vulnerability in supply chains International Journal of Physical Distribution & Logistics Management, 30 (9), 731-750 DOI: 10.1108/09600030010351444
BACK TO POST [2] Svensson, G. (2002). A conceptual framework of vulnerability in firms’ inbound and outbound logistics flows International Journal of Physical Distribution & Logistics Management, 32 (2), 110-134 DOI: 10.1108/09600030210421723
Links
- Halmstad University: Göran Svensson‘s homepage
- nordinavia.se: Göran Svensson’s full professional profile and CV