 So far I have reviewed “international” literature and web sites, and it is only fitting that now it is time for the Norwegian “domestic” literature to be reviewed. Assess the vulnerability of your production system was written back in 1997, by Bjørn Egil Asbjørnslett and Marvin Rausand, both now high-profile academics within risk analysis in Norway.
So far I have reviewed “international” literature and web sites, and it is only fitting that now it is time for the Norwegian “domestic” literature to be reviewed. Assess the vulnerability of your production system was written back in 1997, by Bjørn Egil Asbjørnslett and Marvin Rausand, both now high-profile academics within risk analysis in Norway.
A holistic concept
The paper defines the concept of vulnerability as it applies to production systems and is built around three concepts:
- A taxonomy of vulnerability factors as a basis for or guideline in establishing scenarios
- An input/output model to describe production systems
- A two-step vulnerability analysis for productions systems
I found the paper interesting in many ways, and that is why I decided to take a closer look at it and see if it fits into the context of supply chain vulnerability.
The concept of vulnerability
In 1997 the concept of vulnerability was still relatively unexplored. Resilience and vulnerability are two terms that have grown in both the research literature and the popular literature in recent years, yet, surprisingly, already in 1997, the authors draw a clear line of distinction between the terms vulnerability, robustness and resilience.
A robust or resilient system is able to withstand or absorb disturbances without catastrophic failure and still persist.
Robust means being able to resist an accidental event and return to the same stable situation than before the event. Resilient means being able to return to a new (often “lower”) stable situation than before the event.
The key message is that a robust system will retain its system structure intact, while a resilient system has to adapt to regain a new stable position. There is a distinct notion of severity in these definitions. In a business setting, the ability to survive (resilience) is much more important than the ability to quickly regain stability (robustness).
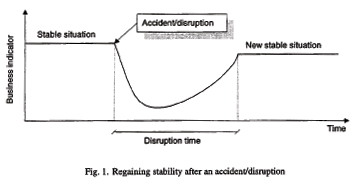
Disruption profile, from: Asbjørnslett (1997)
This figure, taken from the article is very similar to Sheffi’s disruption profile and the description of Resilient Organizations in New Zealand.
Vulnerability factors
The paper distinguishes between two sets of factors, external and internal factors. Within these factors there may be latent threats that can cause potential harm if the factors manifest an accidental event. The figure may not be directly transferable to the realm of supply chains, but one could propose that internal factors are “in-house” or directly controllable, whereas external factors are “out-house” or “outsourced” to use SCM lingo, and only indirectly controllable, if at all controllable.
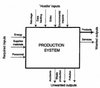
Input/output model
The input/output model, see figure below, is transferable, if, the flow through the production system is replaced with a supply chain going from supplier via focal firm to the customer.
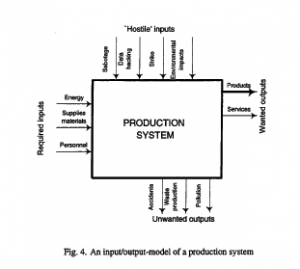
Input-Output Model, from: Asbjørnslett (1997)
The external and internal factors can no be used as a checklist against the inputs (and outputs) and form the basis of a vulnerability analysis. Similarly, these factors can be used vis-a-vis a supply chain, to assess its vulnerability.
Vulnerability versus Risk Analysis
A vulnerability analysis is not the same as a risk analysis. A risk analysis is focused on the human, environmental and property impacts of an accidental event, while a vulnerability analysis is focused towards the survivability of the system.
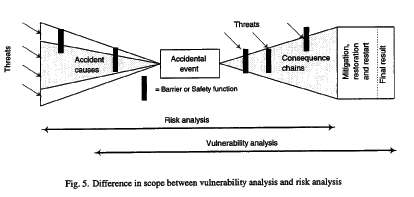
Risk analysis vs. vulnerability analysis, from: Asbjørnslett (1997)
A vulnerability analysis then, focuses on 1) an extended set of threats and consequences, 2) adequate resources to tackle the event and bring the system back to new stability, and 3) the length of disruption before the new stability is established. Clearly, Vulnerability analysis has a wider scope than risk analysis. In particular vulnerability analysis addresses how to mitigate the identified threats and restore and restart the system after an accidental event. This is akin to the distinction between mitigative and contingent actions in Tomlin (2002).
Vulnerability Analysis
Finally then the paper describes the stepped vulnerability analysis. First, a scenario assessment is developed, listing threats and likelihood of potential scenarios and whether or not there are contingent or mitigative measures already in place. Second, a quantitative analysis of the former is performed, ranking threats and scenarios by criticality in terms of human, environmental, business and property impacts. Third, the ranked threats are plotted in a vulnerability matrix similar to the one below.
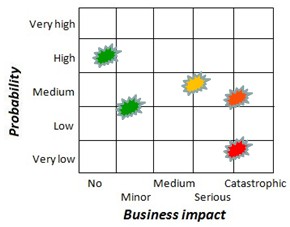
Risk Matrix
The fourth step is to take the most critical events in the vulnerability matrix and list how these threats are to be dealt with, in order to reduce a) the likelihood of the event occurring and b) the consequences should the event occur.
Conclusion
The paper is short, but to the point. Albeit not directly supply chain related, the vulnerability analysis described in this paper can indeed serve as a framework for analysis of supply chain vulnerability, and as such is now in fact widely employed by supply chain risk management professionals. An updated version of this paper has also been published in the book Supply Chain Risk, edited by George Zsidisin and bob Ritchie.
Reference:
Asbjørnslett, B E and Rausand, M (1997) Assess the vulnerability of your production system. Report NTNU 97018. Norwegian University of Science and Technology NTNU, Department of Production and Quality Engineering, Trondheim Norway.
Image 1-3 (Fig. 1+4+5), copyright by Asbjørnslett and Rausand (1997)
Author links
- linkedin.com: Bjørn Egil Asbjørnslett
- linkedin.com: Marvin Rausand
Links
- resorgs.org.nz: Resilient Organisations
- ntnu.no: ROSS – Reliability and Safety Studies
Related
- husdal.com: Risk Management: Contingent versus Mitigative
- husdal.com: Book Review: The Resilient Enterprise
- husdal.com: Book Review: Supply Chain Risk